Maintain Reliability with a
Single-tenant Solution
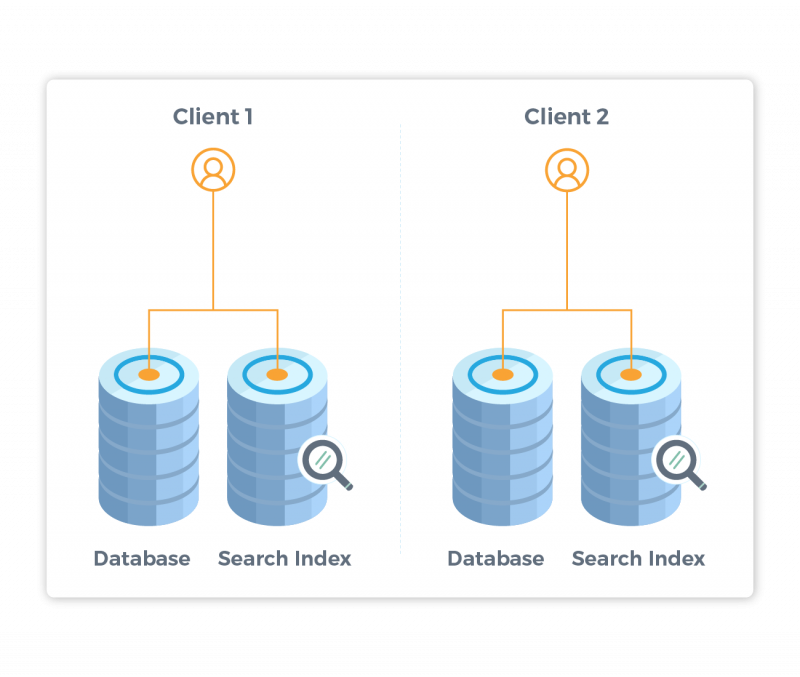
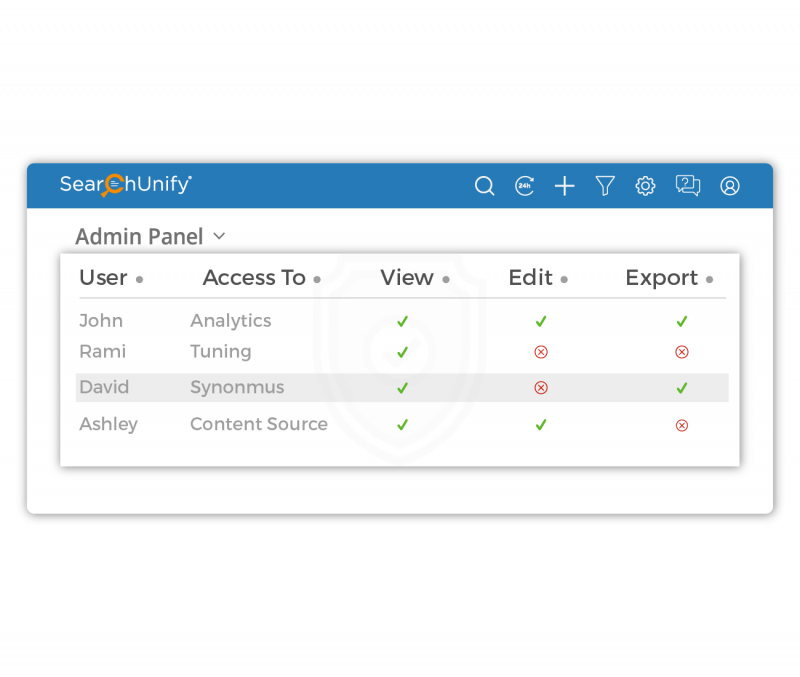
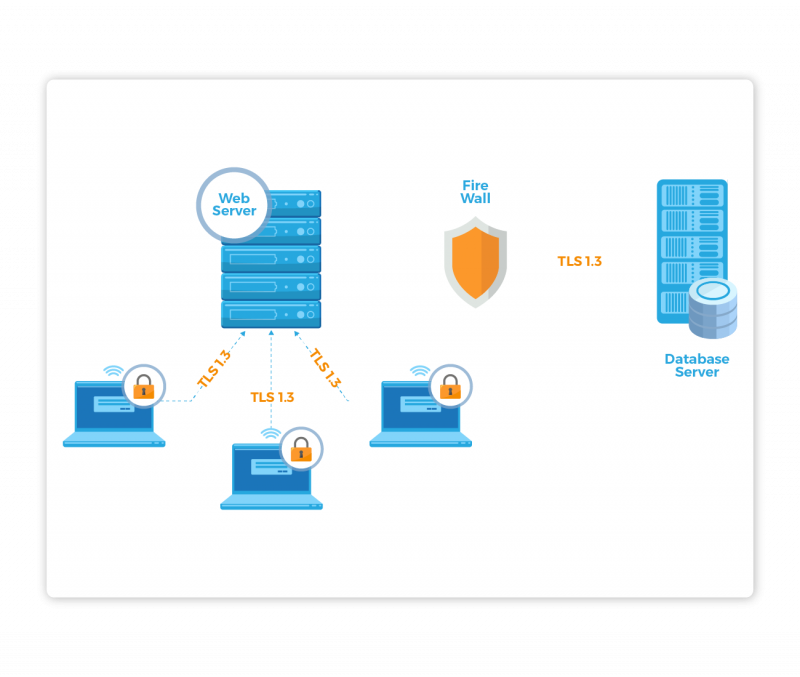
SearchUnify is a single-tenant solution, which guarantees additional security of the content when maintaining its indices and prevents any accidental information leakage.